
In the modern software development lifecycle, where speed and security must go hand-in-hand, integrating tools that support automation and continuous compliance is no longer optional, it’s essential. Developers and DevOps teams are increasingly expected to “shift security left,” embedding security early in the pipeline rather than addressing it as an afterthought. This is where Trivy, a powerful and lightweight open-source vulnerability scanner, plays a pivotal role in improving both DevSecOps workflows and enterprise-grade Security Information and Event Management (SIEM) strategies.
This blog dives deep into how you can utilize Trivy to strengthen your CI/CD pipeline security, automate vulnerability scanning, and integrate security seamlessly into developer workflows, while aligning with the broader objectives of Security Information and Event Management systems.
Let’s explore how Trivy supports DevSecOps goals, why it outperforms traditional scanning tools, and the best practices to follow to ensure maximum security with minimum performance overhead.
As security threats increase in both complexity and volume, organizations must evolve beyond reactive security models. Traditional security workflows typically involved scanning production systems for vulnerabilities and reviewing security logs manually. These models are slow, error-prone, and incompatible with the speed and agility expected in DevOps. In contrast, DevSecOps aims to automate security checks and embed them into every stage of the CI/CD pipeline.
This is where Trivy, built by Aqua Security, has gained widespread popularity among developers. Trivy provides a simple yet comprehensive CLI-based solution that scans:
Its lightweight design, high scanning speed, and wide language support make it an ideal fit for agile development teams practicing DevSecOps. For any organization implementing a Security Information and Event Management strategy, Trivy acts as a reliable input generator, feeding enriched vulnerability data and misconfiguration alerts into the broader SIEM pipeline.
Integrating Trivy into your workflow offers several critical advantages that align with the foundational goals of Security Information and Event Management, centralized visibility, continuous monitoring, and automated threat detection.
1. Shift-left vulnerability scanning
Security Information and Event Management systems rely on timely threat detection, but traditional models detect issues too late in the lifecycle. Trivy helps shift vulnerability detection to the developer phase, before any code even enters a testing or staging environment. This shift not only minimizes the blast radius of a vulnerability but also drastically reduces the cost of fixing it.
2. Lightweight and fast, perfect for CI/CD
Unlike some bulky commercial scanners, Trivy doesn't slow down builds. It’s fast enough to integrate directly into your CI/CD tools (e.g., GitHub Actions, GitLab CI, Jenkins, Bitbucket Pipelines) without causing significant delays. Developers get immediate feedback, which supports continuous integration and continuous delivery without sacrificing security.
3. Extensive scanning capabilities
Trivy doesn’t just detect CVEs in OS packages. It goes much deeper. It scans:
This means you get comprehensive coverage, which improves overall visibility, a central requirement for Security Information and Event Management strategies.
4. Easy integration into SIEM workflows
Trivy scan results can be exported in formats like JSON, which are easily parsed by SIEM tools like Splunk, Elasticsearch, and AWS Security Hub. This makes it simple to aggregate and visualize trends, track recurring vulnerabilities, and monitor compliance across projects and environments.
The true power of Trivy lies in its integration flexibility. No matter your CI/CD platform, you can embed Trivy with a few lines of configuration. Here’s how to do it across the CI/CD pipeline stages, ensuring continuous vulnerability scanning and compliance enforcement.
1. Container Image Scanning during CI builds
When building Docker containers in your pipeline, you can invoke Trivy right after the build step and before deployment. For instance, in GitHub Actions:
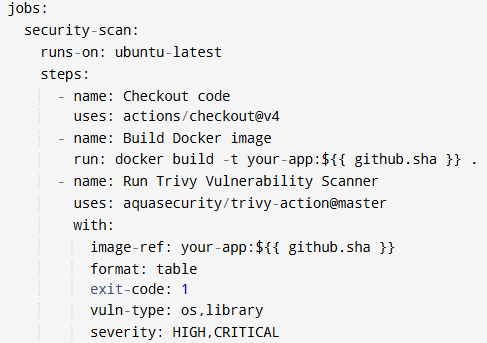
This CI/CD integration ensures the pipeline fails if Trivy detects any high or critical vulnerabilities, enforcing quality gates aligned with your Security Information and Event Management policy.
2. Scanning IaC and Config Files (Filesystem scan mode)
IaC templates are often the source of misconfigured cloud resources. Trivy can analyze these files and alert you to insecure setups, like public S3 buckets or open security groups in Terraform.
trivy config ./infrastructure/
You can insert this step before provisioning infrastructure using Terraform or Pulumi. This ensures that insecure configurations are caught early, another key DevSecOps best practice that feeds into your SIEM for visibility.
3. Infrastructure as Code scan in CI/CD (with severity threshold)
trivy config --severity HIGH,CRITICAL --exit-code 1 ./terraform/
4. Exporting scan reports to SIEM platforms
To fully benefit from Security Information and Event Management, Trivy’s output should be piped into your log ingestion layer:
trivy image --format json -o report.json your-app:latest
cat report.json | curl -X POST -H "Content-Type: application/json" https://your-siem-endpoint/
This enables your DevSecOps team to correlate vulnerability data with user behavior logs, deployment records, and access patterns, all in your SIEM dashboard.
To get the most out of Trivy and ensure alignment with your Security Information and Event Management goals, consider the following best practices:
1. Set strict exit codes for fail-fast builds
CI/CD should halt if Trivy detects high-severity vulnerabilities. This prevents vulnerable code or containers from being deployed accidentally.
2. Use the --ignore-unfixed flag cautiously
While this flag helps avoid blocking pipelines due to unpatched issues, it can hide real risks. Use this only when absolutely necessary and track the ignored CVEs manually in your SIEM logs for future review.
3. Schedule periodic full scans
While CI/CD scans are great, also schedule full scans weekly across deployed images and IaC to catch lingering or new vulnerabilities.
4. Automate Trivy DB updates
Trivy depends on a local vulnerability DB. Automate regular updates using cron jobs or CI tasks to maintain the latest CVE information.
5. Implement policy enforcement
Use Trivy’s built-in policy enforcement capabilities to define what’s allowed and what isn’t, for example, enforcing that all images must have zero HIGH or CRITICAL CVEs before promotion to staging.
Most legacy vulnerability scanners are:
Trivy, on the other hand, is:
This makes Trivy ideal for DevSecOps and an essential contributor to your Security Information and Event Management system.
Trivy’s scan results, when parsed and aggregated across teams, offer valuable insights:
By integrating these insights into your SIEM dashboards, your security team gains centralized visibility into the organization’s vulnerability landscape, accelerating detection and response.
Trivy isn’t just a vulnerability scanner, it’s a DevSecOps enabler that fits perfectly into any CI/CD pipeline and feeds directly into your Security Information and Event Management strategy. With fast feedback, high accuracy, and support for containers, IaC, and application dependencies, Trivy gives developers and security teams the shared visibility they need to ship secure code faster.
By following best practices, such as failing fast on critical issues, automating Trivy in all pipelines, and routing scan data to your SIEM, you create a development ecosystem that prioritizes security without compromising agility.
In a DevSecOps world, tools like Trivy aren't optional. They're foundational.