
In today’s modern development landscape, where distributed systems, containerized workloads, and microservices dominate, traditional access control and authorization mechanisms fall short. Developers and DevSecOps teams are increasingly adopting cloud-native infrastructure, where applications are decoupled, deployed on Kubernetes, and updated frequently. In such dynamic environments, the need for centralized, consistent, and scalable policy-based control is paramount. This is where Open Policy Agent (OPA) steps in, a lightweight, flexible, and powerful policy engine designed for cloud-native architectures.
This blog breaks down OPA in detail, its components, real-world use cases, how it integrates into cloud-native stacks, its benefits over traditional methods, and why it’s become the go-to policy-as-code solution for Kubernetes, CI/CD, APIs, microservices, and beyond. For developers, understanding OPA is no longer optional, it's essential for building secure, auditable, and scalable systems.
Open Policy Agent, or OPA, is an open-source, general-purpose policy engine that allows developers to offload authorization logic from application code into a centralized, declarative policy service. Built for flexibility and extensibility, OPA enables teams to define policies-as-code using a purpose-built language called Rego.
OPA was created by Styra and is now a CNCF-graduated project. Unlike traditional, hardcoded if-else statements scattered across multiple services, OPA lets you write and manage policies in one place, test them, deploy them safely, and update them without touching business logic.
OPA’s main function is to evaluate input data, typically from a service request, and return a decision. This could be something simple like “allow” or “deny” or more complex like structured JSON responses. OPA is vendor-neutral, lightweight, and highly embeddable, making it ideal for microservices, Kubernetes admission control, API gateways, infrastructure-as-code (IaC) tools, and serverless functions.
OPA is not just for security engineers or operations teams, it’s designed with developers in mind. Here’s why it’s become a favorite among dev teams building for scale and security.
With OPA, developers can decouple policy decisions from application logic. This means that business logic remains clean and focused, while policies related to security, compliance, and governance are managed separately in version-controlled, testable files. This separation improves maintainability and simplifies collaboration between development and security teams. It also aligns well with GitOps workflows, allowing policies to be reviewed, versioned, and deployed using the same CI/CD tools used for application code.
OPA provides a unified model for policy enforcement, enabling you to reuse the same policies across Kubernetes admission controllers, API gateways, service meshes, CI/CD pipelines, infrastructure provisioning tools like Terraform, and more. This reduces redundancy and inconsistency. By centralizing policy logic in OPA, you ensure that the same security and compliance rules are applied consistently everywhere, from the time code is written, to when it is deployed, and even during runtime.
OPA is a small, embeddable binary (≈2MB), making it easy to include in container images or sidecar containers. It compiles policies into optimized evaluation plans and caches them in memory, leading to sub-millisecond decision times in most environments. This makes it ideal for real-time authorization, even under heavy workloads.
Every decision OPA makes can be logged with rich context about the input, policy version, and outcome. This enables fine-grained auditing and visibility into policy enforcement, a key requirement for regulated industries like finance, healthcare, and insurance. Logs can be streamed into centralized observability platforms (e.g., ELK, Prometheus, OpenTelemetry) to support incident response and compliance audits.
OPA is highly flexible. You can embed it directly into your application using the Go SDK, run it as a daemon service, deploy it as a sidecar in Kubernetes, or host it in a remote service that is queried via REST. This allows you to choose the architecture that best fits your system’s latency, reliability, and isolation requirements.
Because OPA is open-source and platform-agnostic, it can be used in any cloud provider, hybrid setup, or even on-prem. It’s not tied to a particular vendor or infrastructure toolchain, which makes it a great long-term investment for teams looking to avoid lock-in and build adaptable systems.
At the heart of OPA lies its policy language, Rego. Rego is a declarative, purpose-built language designed to express complex logic over JSON-like data structures. It’s used to write rules that evaluate inputs, consult external data, and produce decisions.
Example:
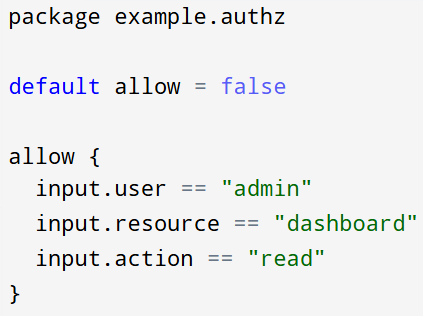
OPA evaluates this policy using the provided input. If the conditions are met, the policy returns true for allow.
OPA works by loading policies and data into memory and exposing an API for policy queries. When queried, it evaluates policies against input data and returns a decision.
OPA is designed to be versatile. Here are common real-world use cases that demonstrate its utility:
OPA was built for developers who need scalable, secure, and testable policy enforcement.